Photo by Audrius Sutkus on Unsplash
Since I joined Pure Storage - over 2 years now - I started mainly focusing on Pure Cloud Block Store and its use cases, I have been learning and using Terraform to do mostly all the repeatable tasks in the public cloud, from infrastructure deployment to resource management. Terraform as a tool is easy to use, authenticate to the cloud provider, describe your infrastructure, and hit apply. However, there is an art of using Terraform to create reusable code, with a sense of abstraction where you can describe your infrastructure in terms of its architecture, rather than directly in terms of resources objects.
In this blog post I will showcase how I leveraged the art of Terraform Modules for building a couple of examples for provisioning Pure Cloud Block Store prerequisite, deploying the array as standalone or managed by Pure Fusion. Let’s get into the details.
Starting point
This blog and Terraform code covers Pure Cloud Block Store deployment in Azure only. AWS work are in progress.
Last year David Stamen wrote the Terraform Quick Launch for CBS. I jumped to use it of course, and it became the preferred way for testing new CBS releases, or delivering a PoC.
On parallel I started breaking the code into modules. Rather than having one main.tf with multiple resources, it was hard sometimes to abstract the infrastructure (VNet, NAT GW, Managed Identity) from the CBS array resource or sharing infra to multiple CBSs without screwing the state if you deleted one CBS.
Modules are the main way to package and reuse resource configurations with Terraform. The table below shows the modules I have put together, then I call those modules from the root modules in terms of “Deploy-*” examples
| Module Name | Functionality |
|---|---|
| CBS-VNET | Creates an Azure VNet with four Subnet |
| CBS-NAT-GW | Creates an Azure NAT GW and associate it with CBS System Subnet |
| CBS-Key-Vault | Creates an Azure Key Valut that is used by CBS Terraform Provider to perform management operations |
| CBS-Identity | Creates an Azure Custom Role and Assign it to a User Managed Identity |
| VM-JUMPBOX | Creates an Azure VM on the same CBS VNet, it can be used as a Jump Host or repurpose as an initiator |
| CBS-Array | Creates a Cloud Block Store Array |
| Fusion-SEC | Create a Fusion Storage Endpoint Collection |
| Fusion-CBS-Array | Creates a Cloud Block Store Array that can be associated to a Fusion SEC |
Before you Start
You should have or prepared the following:
- Have an Azure Subscription you can authenticate to using Az login or Service Priniciple.
- Select Supported region. You can find a list of regions here.
- Deploy an Azure VM in the same subscription where you are planning to deploy CBS. Then SSH to the VM.
The reason for deploying the VM in Azure is to establish network connectivity between the Azure VM VNet and the CBS VNet created in the example. The VNet Peering is part of the modules created, you just need to pass the Azure VM VNet id and resource group, and it would be automatically configured for you.
- Clone the repo:
git clone https://github.com/adammazouz/Pure-CBS-Terraform-Modules.git
Example 1: Deploy-CBS-Prerequisits-Only
The main use case for this example is to offer an easy workflow for those who want to PoC or demonstrate deploying Pure CBS from the Azure portal and don’t want to spend time creating all the prerequisite. One click to deploy all the required resource just 5 minutes before your demonstration, neat ain’t it!
- Once you have cloned the repo, navigate to the directory:
cd Pure-CBS-Terraform-Modules/deploy-CBS-Prerequisites-Only
- Modify the
terraform.tfvarsfile with your own naming and VNet/Subnets IP ranges.
vi terraform.tfvars
- Hit
terraform init, thenterraform apply. Thats it! You can find navigate to Azure Portal, search for the Resource Group to find all the resources.
Example 2: Deploy-CBS-Greenfield
This example deploys both the prerequisite and CBS array. it takes from 15 to 20 minutes to finish a successful deployment, and it outputs all the CBS interfaces endpoint IPs (Management, iSCSI, Replication), besides the public and private IP address of the VM used as a JumpBox or a storage initiator.Your choice!
CBS Greenfield is a term I used here to refer to Standalone CBS since I am working on Cloud Block Store managed by Fusion in the next examples. if you have better name for it, reach out or leave a comment below.
- Similar to the previous example, once you have cloned the repo, navigate to the directory:
cd Pure-CBS-Terraform-Modules/deploy-CBS-Prerequisites-Only
- Then modify the
terraform.tfvars. On top of the prerequisite variable, you would need to select a couple of CBS variables.
| CBS Variable | Description |
|---|---|
| license_key | Pure Cloud Block Store License Key, you can use CBS-TRIAL-LICENSE for 45 days evaluation mode, more info here |
| log_sender_domain | Domain to be used for CBS, ex: purestorage.com |
| alert_recipients | Email Address to be used for CBS Alerts |
| array_model | CBS Model (V10MUR1 or V20MUR1 or V20MP2R2) |
| zone | Zone in Region to deploy (1,2 or 3), Check before you select thr zone, some regions do not have support for Ultra SSD or PremiumV2, more info here |
| groups | Azure AD Group id for JIT Approval |
| New key_file_path | Private Key File Path for pureuser |
- Hit
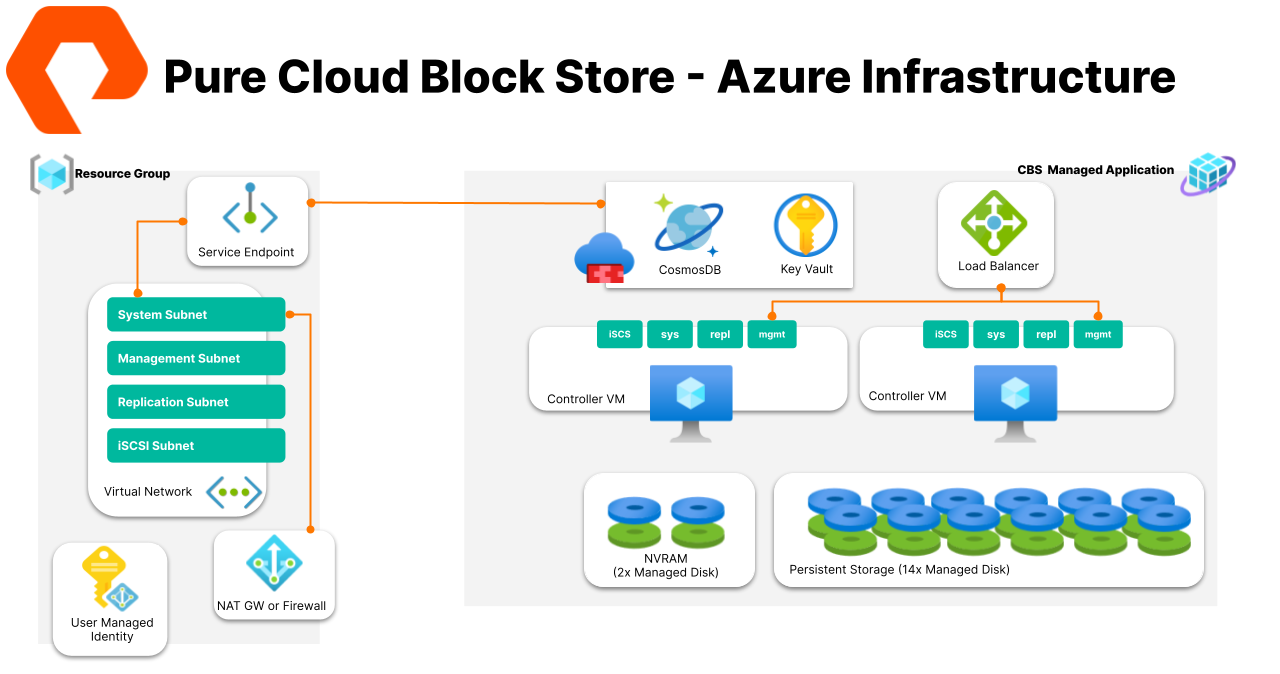
terraform init, thenterraform apply. Terraform will deploy and configure all the resource you can see in the diagram below.
So, What is next?
A couple of things really, mostly finishing Fusion Provider example for an end-to-end CBS + Fusion workflow.
The other thing I will look into is how to wrap those examples with a CLI tool. Something like:
purecbstf deploy cbs_standalone –tfvar_file_path /home/amazouz/terraform.tfvars –project test_cbs
or
purecbstf list –project test_cbs
or
Purecbstf destroy –project test_cbs
Many other exciting stuff coming for Pure Cloud Block Store, we have only just begun to scratch the surface.
comments powered by Disqus